How to Configure STSAssumeRoleSessionCredentialsProvider in Spring Cloud Stream Kinesis Binder
Автор: vlogize
Загружено: 2025-10-06
Просмотров: 1
Описание:
Learn how to effectively configure `STSAssumeRoleSessionCredentialsProvider` within your Spring Cloud Stream Kinesis Binder setup to access Kinesis streams across AWS accounts.
---
This video is based on the question https://stackoverflow.com/q/64015952/ asked by the user 'Darshan Gandhi' ( https://stackoverflow.com/u/14323035/ ) and on the answer https://stackoverflow.com/a/64016970/ provided by the user 'Artem Bilan' ( https://stackoverflow.com/u/2756547/ ) at 'Stack Overflow' website. Thanks to these great users and Stackexchange community for their contributions.
Visit these links for original content and any more details, such as alternate solutions, latest updates/developments on topic, comments, revision history etc. For example, the original title of the Question was: How to Configure using STSAssumeRoleSessionCredentialsProvider in spring-cloud-stream-binder-kinesis
Also, Content (except music) licensed under CC BY-SA https://meta.stackexchange.com/help/l...
The original Question post is licensed under the 'CC BY-SA 4.0' ( https://creativecommons.org/licenses/... ) license, and the original Answer post is licensed under the 'CC BY-SA 4.0' ( https://creativecommons.org/licenses/... ) license.
If anything seems off to you, please feel free to write me at vlogize [AT] gmail [DOT] com.
---
How to Configure STSAssumeRoleSessionCredentialsProvider in Spring Cloud Stream Kinesis Binder
When working with Amazon Kinesis in a Spring Cloud application, you might face challenges related to accessing Kinesis data streams across different AWS accounts. This guide addresses a common issue: how to configure the STSAssumeRoleSessionCredentialsProvider in spring-cloud-stream-binder-kinesis, particularly when your Kinesis data streams are hosted in one AWS account and your application is running in a different one.
The Challenge
If you've been using spring-cloud-stream-binder-kinesis, you probably relied on the default ContextCredentialsAutoConfiguration for local development, which works well in simpler setups. However, complications arise when:
Your Kinesis data stream resides in AWS Account 1.
Your Spring Cloud application is running in AWS Account 2.
In scenarios like this, you need to transition from using default credentials to an STSAssumeRoleSessionCredentialsProvider that allows your application to assume a role in Account 1 to access its Kinesis streams.
The Solution
Configuring the STSAssumeRoleSessionCredentialsProvider in your Spring application involves a few straightforward steps. Let's break it down:
1. Understanding KinesisBinderConfiguration
The KinesisBinderConfiguration in Spring depends on auto-configuration provided by Spring Cloud AWS. This setup typically creates and exposes an AWSCredentialsProvider bean. If you haven't defined any specific credentials provider, the default setup uses the standard context credentials.
2. Defining the Credentials Provider
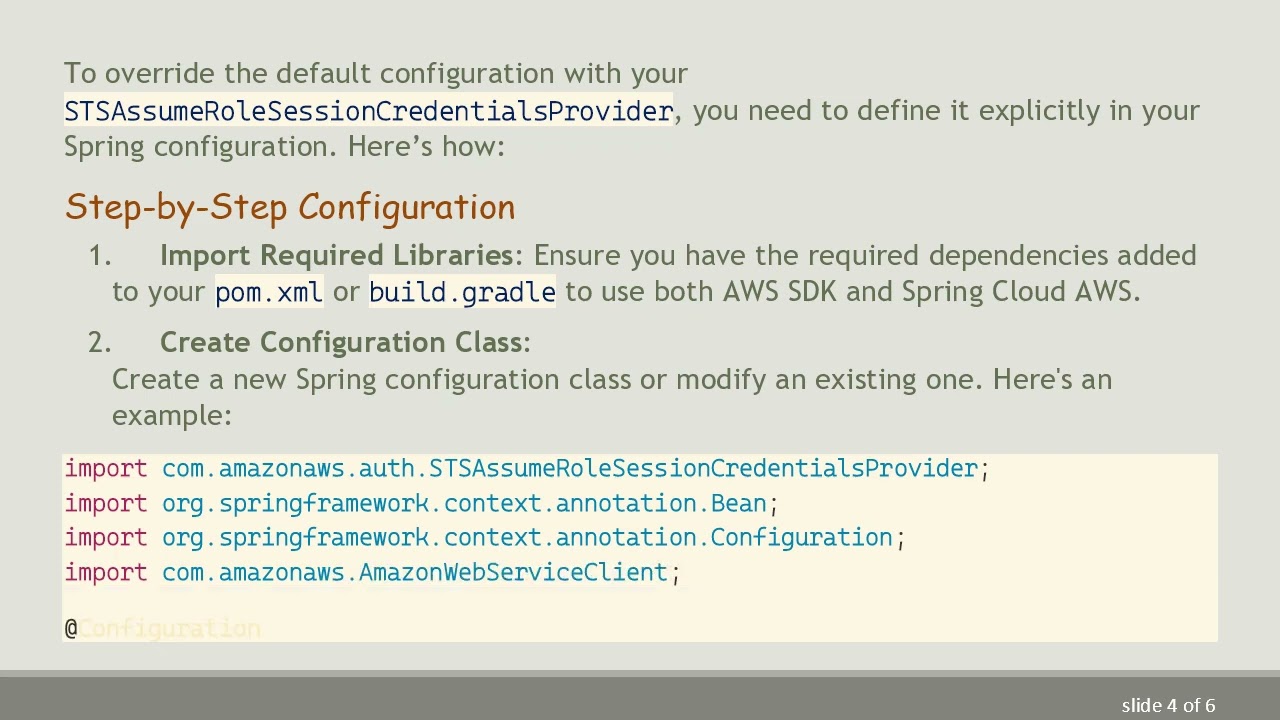
To override the default configuration with your STSAssumeRoleSessionCredentialsProvider, you need to define it explicitly in your Spring configuration. Here’s how:
Step-by-Step Configuration
Import Required Libraries: Ensure you have the required dependencies added to your pom.xml or build.gradle to use both AWS SDK and Spring Cloud AWS.
Create Configuration Class:
Create a new Spring configuration class or modify an existing one. Here's an example:
[[See Video to Reveal this Text or Code Snippet]]
Replace ACCOUNT_ID and ROLE_NAME with your actual AWS account ID and the name of the role you want to assume.
The withRoleSessionName can be any string that helps you identify the session.
Specify the Bean Name: Make sure that the bean's name matches credentialsProvider so it gets picked up correctly by Spring Cloud Stream Kinesis Binder.
3. Testing Your Configuration
After setting up your configuration, you can run your Spring Cloud application. If configured correctly, your application will assume the specified role in Account 1 and gain access to the Kinesis data streams.
Conclusion
Configuring the STSAssumeRoleSessionCredentialsProvider for Spring Cloud Stream Binder Kinesis allows your AWS resources to communicate securely across different accounts. By following the steps outlined in this guide, you can effectively manage access between your applications and AWS services without compromising security.
Feel free to reach out for any further questions or clarification as you set up your environment!
Повторяем попытку...
Доступные форматы для скачивания:
Скачать видео
-
Информация по загрузке: