Cryptography Challenge
Автор: Sukhraj Dhindsa
Загружено: 2014-10-18
Просмотров: 397
Описание:
Cryptography Challenge
TEJ2O0-A, Castlebrooke SS
Peel District School Board
2014-10-20
Jay, Paul, Sukhraj, Tanish
We were the winning group in the Cryptography Challenge in Mr. Anderson’s grade 10 Computer Technology class.
The challenge explained:
There were 8 groups in the class, and each was given a text. They were to create a key to encrypt the text. All of the encrypted messages were distributed to the 8 groups, and we were to attempt to break encryptions with logic, subterfuge and online analytical tools. We were able to use any and all methods to encrypt and decrypt (besides violence). The winner of the group received $56.
How we came up with the numbers used in the first encryption:
We used a formula.
10xπ
And x represented the prime number that matched the letter we were trying to change, in chronological order. For example, A used 2, B used 3, C used 5, D used 7, E used 11, etc.
After we obtained an answer, we rounded to the nearest one.
Glossary:
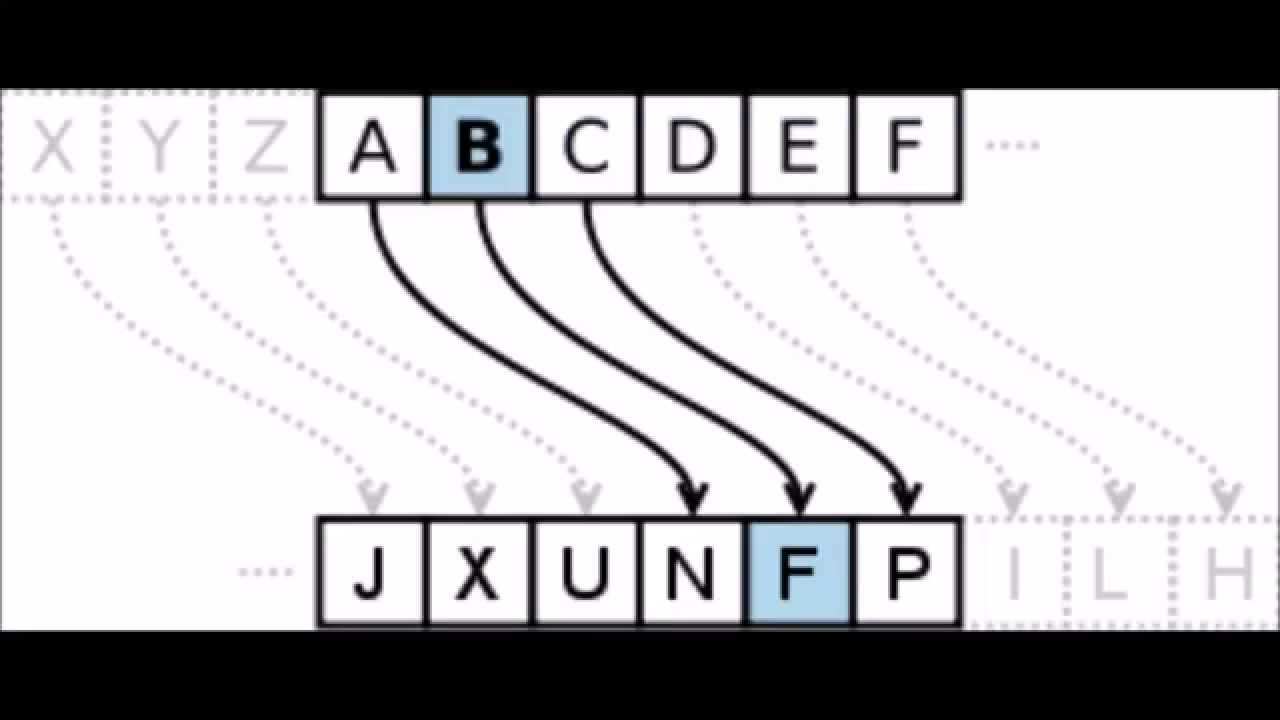
Substitution – Replacing characters with different characters
Key - Information that changes the input of a message into a cryptographic output. The key is required for the message to be ciphered. The key allows control over encryption and decryption.
Online Resource about Substitution
http://www.princeton.edu/~achaney/tmv...
Повторяем попытку...
Доступные форматы для скачивания:
Скачать видео
-
Информация по загрузке:









