Exploring Pseudo Access on Your System! 🖥️
Автор: Bash Explorer
Загружено: 2025-10-20
Просмотров: 1395
Описание:
Master Linux root access security with this comprehensive practice series! This short is part of a complete hands-on tutorial covering essential system administration commands and security best practices for Red Hat Enterprise Linux, CentOS, and other enterprise Linux distributions.
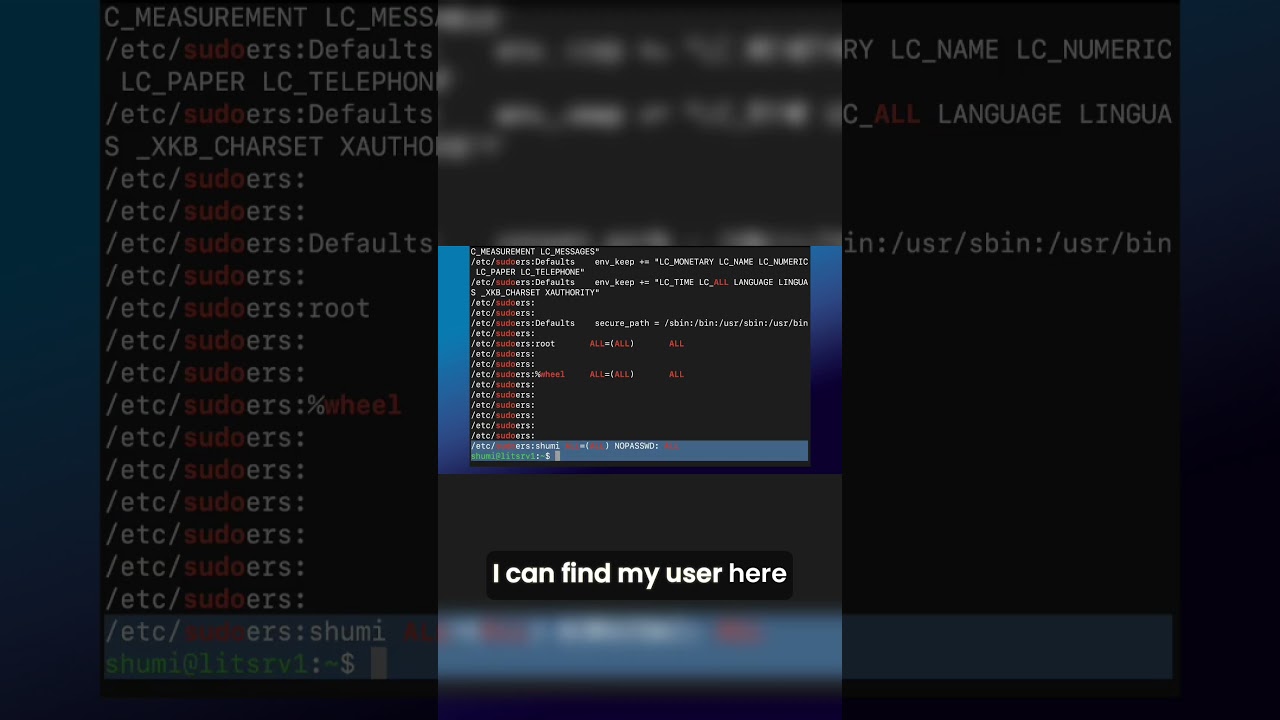
In this series, you will learn critical skills for managing root access and user privileges securely. We cover the fundamental differences between su and sudo commands, demonstrating why sudo is the preferred method in modern Linux security practices. You'll see practical implementations of secure command execution, learn how to properly audit and configure sudoers files, and understand how to manage user permissions effectively.
The series includes detailed walkthroughs of examining root account status using shadow file entries, creating and managing test users with elevated privileges, implementing proper login shell environments, and conducting comprehensive security audits of your system's privilege escalation configurations. Each short demonstrates real terminal commands with actual output, giving you the practical experience needed for system administration roles.
Whether you're preparing for Red Hat certifications like RHCSA or RHCE, working as a system administrator, or building your DevOps skills, this practice series provides essential knowledge for securing Linux systems in production environments. Perfect for beginners learning Linux security fundamentals and experienced administrators wanting to reinforce best practices.
#LinuxSecurity #RootAccess #SudoCommand #SuCommand #RHEL #RedHat #LinuxShorts #SystemAdministration #CyberSecurity #DevOps #LinuxTutorial #SecurityBestPractices #UserPrivileges #LinuxCommands #SysAdmin #ITSecurity #LinuxTraining #EnterpriseLinux #Shorts #TechShorts
Повторяем попытку...
Доступные форматы для скачивания:
Скачать видео
-
Информация по загрузке: