Understanding SQL Injection: Tautology vs. Blind Attacks.|
Автор: Mr. K Talks Tech
Загружено: 2025-10-21
Просмотров: 1538
Описание:
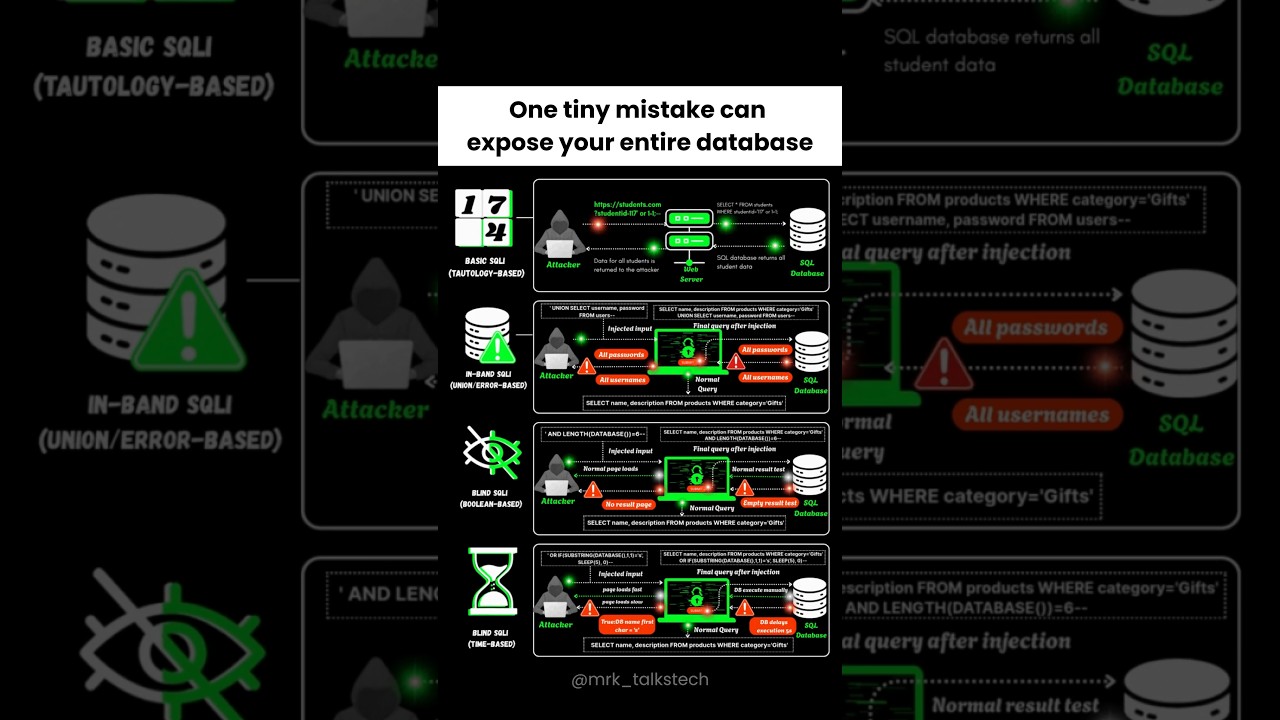
One "tiny mistake" is all it takes to expose your ENTIRE database. 💻
This video is a 60-second guide to SQL Injection (SQLi), one of the most common and dangerous security vulnerabilities on the web. We break down the four primary ways hackers use SQLi to bypass logins, steal user passwords, and dump all your data.
In this short, you'll see:
1️⃣ IN-BAND SQLi (Tautology-Based): The classic 'OR 1=1' trick to bypass a login.
2️⃣ IN-BAND SQLi (Union-Based): How attackers use `UNION SELECT` to steal data from other tables.
3️⃣ BLIND SQLi (Boolean-Based): A stealthy method of asking the database true/false questions to guess data.
4️⃣ BLIND SQLi (Time-Based): How attackers use `SLEEP()` commands to infer data based on the server's response time.
This is the #1 security flaw every web developer, programmer, and cybersecurity enthusiast needs to understand. Never trust user input!
🔔 Subscribe for more tech and cybersecurity tips!
#sqlinjection #cybersecurity #hacking #programming #webdevelopment #ethicalhacking #sql #coding #infosec #shorts
Повторяем попытку...
Доступные форматы для скачивания:
Скачать видео
-
Информация по загрузке: