Khairul Hafidh

Produk Shopee bermasalah 3D printing, file kebesaran max 10MB

PEKERTI-USY

Aplikasi di Bidang Informatika Biomedis

FORENSICS & CYBERSECURITY TOOLS||WHOIS

FORENSICS TOOLS||RAW LOG FORENSICS||RAW TEXT

FORENSICS & CYBERSECURITY TOOLS||NSLOOKUP

FORENSICS TOOLS||RAW LOG FORENSICS||RAW IMAGE

FORENSICS TOOLS||TEXT PARSER||NLP FORENSICS

FORENSICS TOOLS||TEXT PARSER||USB LOOKUP

FORENSICS TOOLS||NETWORKING & INDICATORS OF COMPROMISE||WAL CRAWLER

FORENSICS TOOLS||NETWORKING & INDICATORS OF COMPROMISE||BEAUTIFUL PRESERVATION & CLONNING SITE

FORENSICS TOOLS||NETWORKING & INDICATORS OF COMPROMISE||IEF PARSER

FORENSICS TOOLS||NETWORK TRAFFIC ANALYSIS||TEST DOMAIN FLUX

FORENSICS TOOLS||NETWORK TRAFFIC ANALYSIS||TEST FAST FLUX

FORENSICS TOOLS||NETWORK TRAFFIC ANALYSIS||GOOGLE EARTH PCAP

FORENSICS TOOLS||NETWORK TRAFFIC ANALYSIS||GEO PRINT

FORENSICS TOOLS||NETWORK TRAFFIC ANALYSIS||PRINT DIRECTION

FORENSICS TOOLS||NETWORK TRAFFIC ANALYSIS||GEO IP

FORENSICS TOOLS||FORENSIC INVESTIGATIONS||BROWSER FORENSICS|

FORENSICS TOOLS||MOBILE FORENSICS||SQLITE PARSER||

FORENSICS TOOLS||MOBILE FORENSICS||PLIST PARSER||
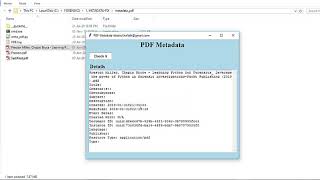
FORENSICS TOOLS||METADATA||PDF METADATA||

FORENSICS TOOLS||METADATA||ZIP METADATA||

FORENSICS TOOLS||METADATA||DOCUMENT METADATA||

FORENSICS TOOLS||METADATA||EXECUTABLE METADATA||

FORENSICS TOOLS||METADATA||PICTURE METADATA||

INTRODUCTION TO CYBERSECURITY | CISCO COURSE | CHAPTER 5 - WILL YOUR FUTURE BE IN CYBERSECURITY|

INTRODUCTION TO CYBERSECURITY | CISCO COURSE | CHAPTER 4 - PROTECTING THE ORGANIZATION

INTRODUCTION TO CYBERSECURITY | CISCO COURSE | CHAPTER 3 - PROTECTING YOUR DATA & PRIVACY|

INTRODUCTION TO CYBERSECURITY | CISCO COURSE | CHAPTER 2 - ATTACKS, CONCEPTS & TECHNIQUES|